Introduction
Upgrading from Windows 10 to Windows 11 sounds simple on paper: click, install, done. But anyone who has managed more than three machines knows that reality is… different. Devices argue, policies complain, and users suddenly “forget” their password the moment you schedule a reboot.
That’s where Microsoft Intune comes in. Think of it as your friendly robot assistant — except it won’t spill coffee on the server rack or call in sick on patch Tuesday. With the right setup, Intune can handle the heavy lifting, making your Windows 11 rollout less like a horror movie and more like a well-scripted Netflix series.
This guide will walk you through hardware requirements, upgrade policies, and even a troubleshooting script for those devices that behave like stubborn teenagers.

Requirement – to Deploy Windows 11 Through Intune
Upgrading from Windows 10 to Windows 11 via Microsoft Intune requires your devices to meet certain hardware and software prerequisites. Let’s walk through the necessary steps to ensure a seamless upgrade!
1. Hardware Compatibility
Before diving into the upgrade process, make sure your devices meet the following minimum requirements:
- Processor: A compatible 64-bit processor with at least 1 GHz clock speed and 2 or more cores.
- Memory (RAM): At least 4 GB.
- Storage: 64 GB or more of available disk space.
- System Firmware: UEFI, Secure Boot capable.
- TPM: Trusted Platform Module (TPM) version 2.0.
- Graphics Card: DirectX 12 compatible graphics / WDDM 2.x driver.
- Display: Greater than 9” with HD Resolution (720p).
2. Current Windows Version
Your device should be running Windows 10, version 2004 or later to upgrade to Windows 11. If you’re still on an older version, you’ll need to update to at least 2004 before proceeding.
3. Previous Windows Updates
Ensure that all critical security and system updates are installed before you begin the upgrade process. This step is essential for ensuring that Windows 11 installs properly.
4. Compliance in Intune
The device must be compliant with the security policies enforced by Microsoft Intune. This includes:
- Password requirements
- Disk encryption (BitLocker)
- Threat protection policies
Additionally, the device must be enrolled in Intune MDM and be Hybrid AD joined or Azure AD joined.
By ensuring all these prerequisites are met, you can smoothly transition your devices to Windows 11 using Intune.
Setting Up the Upgrade Policy in Intune
Now that your devices are ready for the upgrade, let’s dive into setting up a policy to deploy Windows 11 / 23H2 through Intune.
Intune offers three main options for pushing feature updates:
- ASAP (as soon as possible)
- On a specific date
- Gradually – where Intune will select random devices from the assigned group (or all devices) and set a delay between groups.
Let’s go step by step on how to set this up:
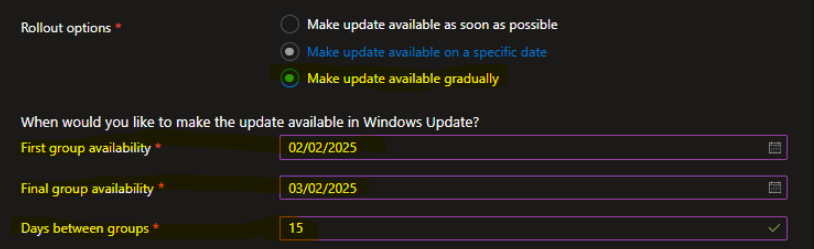
- Choose Your Deployment Settings
Set your first group to upgrade on February 2nd, and your final group’s upgrade should be available by March 6th. That gives us a 30-day window to push the upgrade to all devices. If you set a delay between groups (let’s say 15 days), Intune will divide the devices into two groups for staggered deployment.
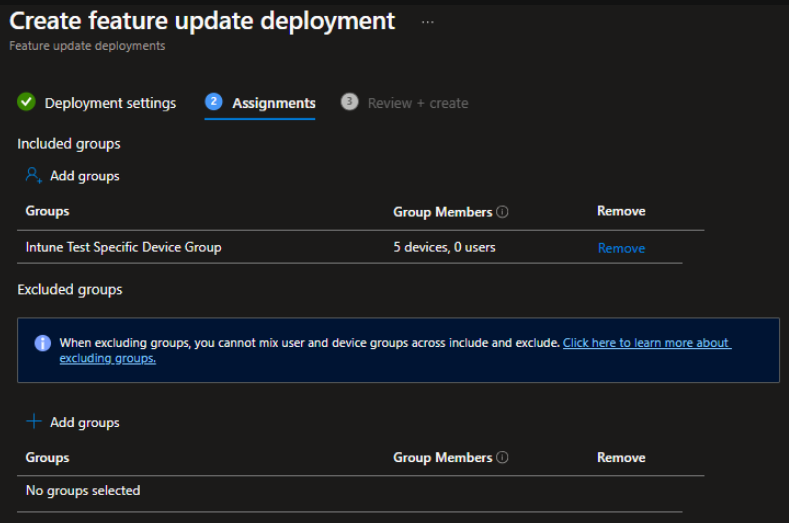
- Assign Groups
Now assign the group of devices you want to deploy the update to. Once done, hit Next.
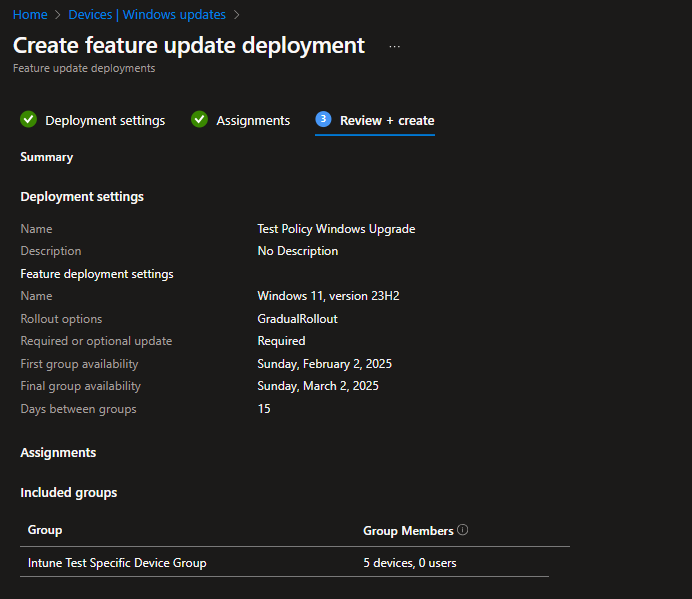
- Review and Create
Review the settings and hit Create to apply the policy.
Now, just sit back and let Intune take care of the upgrade process!
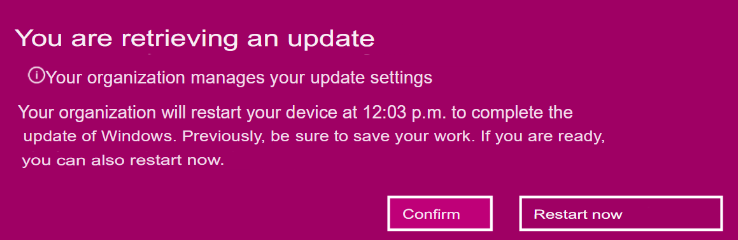
Understanding the Update Process: Restart and Grace Period
Once the update is pushed, the device will receive and download the update, but the actual installation and restart behavior will depend on your Feature Update Ring policy.
How Windows Manages the Update Installation and Restart
- User-initiated restart: If users are allowed to restart at their convenience, they may delay it.
- Grace Period (if configured): If a grace period is set in the update ring policy, users will be given a certain number of days to restart their devices before Windows forces the update.
- Forced Restart: If the grace period expires, Windows will automatically install the update and restart the device.
What You Need to Do
- Check the existing Feature Update Ring policy:
- Go to Intune Admin Center → Devices → Windows Update Rings and review your settings.
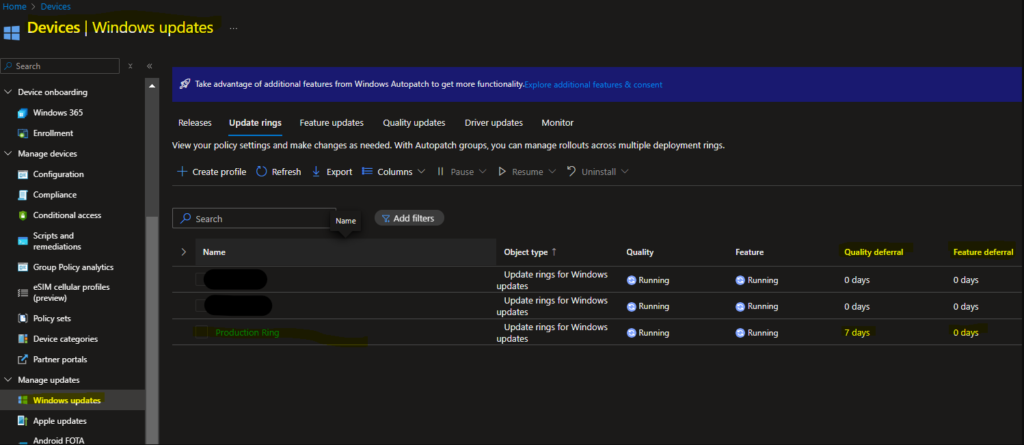
- If no policy is set, you need to create a new Feature Update Ring with a proper balance between user experience and security.
- Adjust the grace period to define how long users have before Windows enforces the update.
let’s take our exemple « pay attention to the underline yellow »:
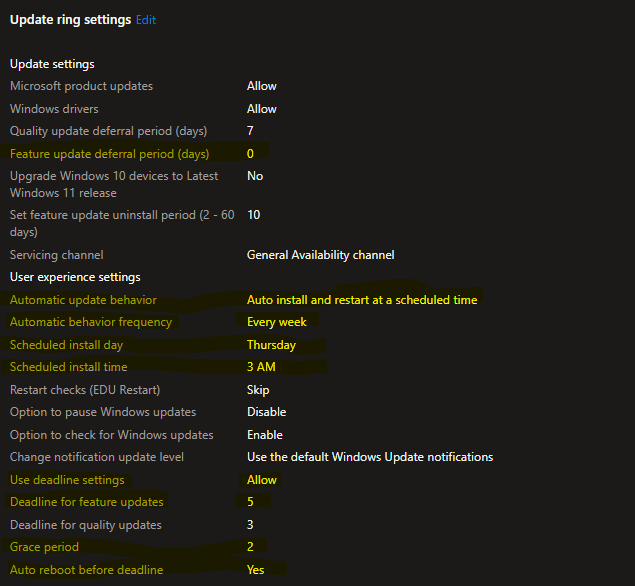
- Explaination: if a feature update is available « 0 » days mean it will be sstarting from the day 1 available to users
- each Trsday at 3AM a check update will be lunched by the inutne management extention each week
- deadline for feature updates to be installed it’s « 5 days »
- and windows will give « 2 more days » as a grace periode « a delay »
- in total we have 7 days to apply the feature updates and after the deadline windows will force restarting the device to apply the feature updates
By properly configuring these settings, you can avoid unnecessary downtime and ensure a smoother transition for your users.
Troubleshooting the Upgrade
In case any issues arise, you may face challenges such as devices failing to update or Windows Update errors
you can review windows update for devices under Reports | Endpoint Analytics > Work from anywhere > Windows
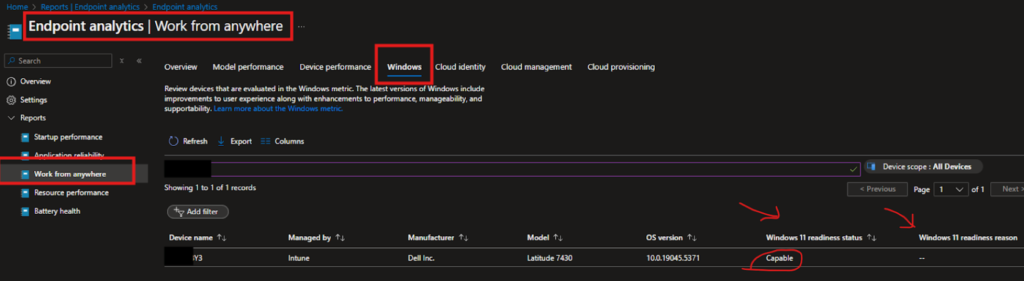
In case of issue I’ve prepared a remediation script that will help fix common update issues.
What the Remediation Script Does:
- Stops the Windows Update services.
- Clears the Windows Update cache.
- Restarts necessary services.
- Runs system file repair (SFC & DISM).
- Resets the Windows Store cache.
- Forces a Windows Update check.
Deploying a Remediation Script via Intune
If the upgrade isn’t applying smoothly, you can deploy a remediation script through Intune to ensure devices are fixed automatically. Here’s how to configure and deploy the script.
Remediation Script:
Fix any issues by restarting services, clearing cache, and triggering the update check.
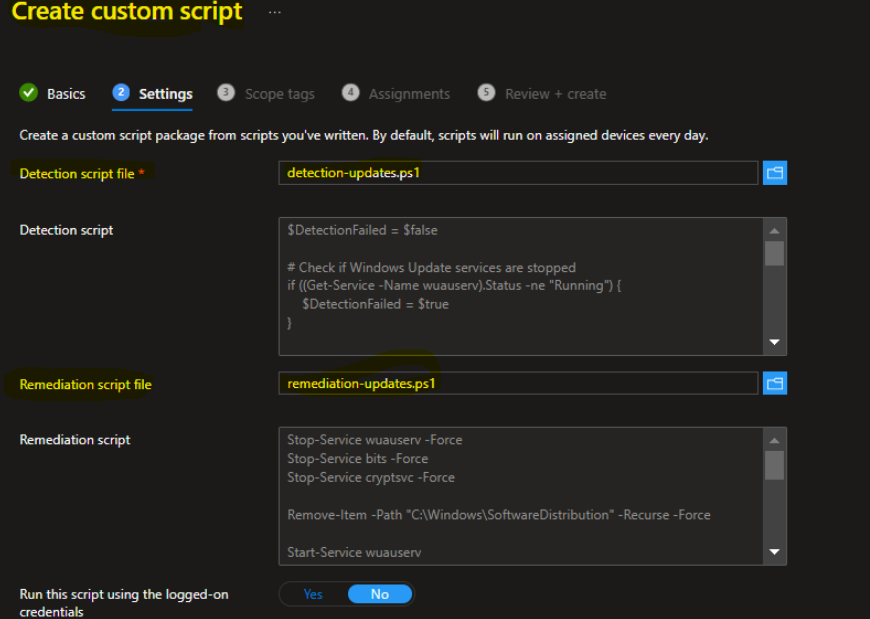
Here’s the PowerShell script for detection:
$DetectionFailed = $false
# Check if Windows Update services are stopped
if ((Get-Service -Name wuauserv).Status -ne "Running") {
Write-Output "Detection failed: Windows Update service is not running."
$DetectionFailed = $true
}
if ((Get-Service -Name bits).Status -ne "Running") {
Write-Output "Detection failed: Background Intelligent Transfer service is not running."
$DetectionFailed = $true
}
if ((Get-Service -Name cryptsvc).Status -ne "Running") {
Write-Output "Detection failed: Cryptographic service is not running."
$DetectionFailed = $true
}
# Check if SoftwareDistribution folder exists
if (!(Test-Path "C:\Windows\SoftwareDistribution")) {
Write-Output "Detection failed: SoftwareDistribution folder is missing."
$DetectionFailed = $true
}
# Return detection result
if ($DetectionFailed) {
Write-Output "Detection rule: Failure"
exit 1 # Return failure code
} else {
Write-Output "Detection rule: Success"
exit 0 # Return success code
}
And here’s the remediation script:
# Run as Administrator
Write-Output "🔧 Stopping Windows Update services..."
Stop-Service wuauserv -Force
Stop-Service bits -Force
Stop-Service cryptsvc -Force
Write-Output "🧹 Cleaning Windows Update Cache..."
Remove-Item -Path "C:\Windows\SoftwareDistribution" -Recurse -Force
Write-Output "✅ Restarting Windows Update services..."
Start-Service wuauserv
Set-Service wuauserv -StartupType Automatic
Start-Service bits
Set-Service bits -StartupType Automatic
Start-Service cryptsvc
Set-Service cryptsvc -StartupType Automatic
Write-Output "🔍 Running System File Checker (SFC)..."
sfc /scannow
Write-Output "🛠 Running DISM to repair Windows image..."
DISM /Online /Cleanup-Image /RestoreHealth
Write-Output "🛒 Resetting Windows Store Cache..."
Start-Process -FilePath "wsreset.exe" -Wait
Write-Output "🔄 Searching for Windows Updates..."
# Forces a Windows Update check
Start-Process -FilePath "cmd.exe" -ArgumentList "/c wuauclt /detectnow" -Wait -NoNewWindow
Start-Process -FilePath "cmd.exe" -ArgumentList "/c wuauclt /reportnow" -Wait -NoNewWindow
Write-Output "✅ System repair and Windows Update search completed!"
Steps to Deploy the remediation script in Intune:
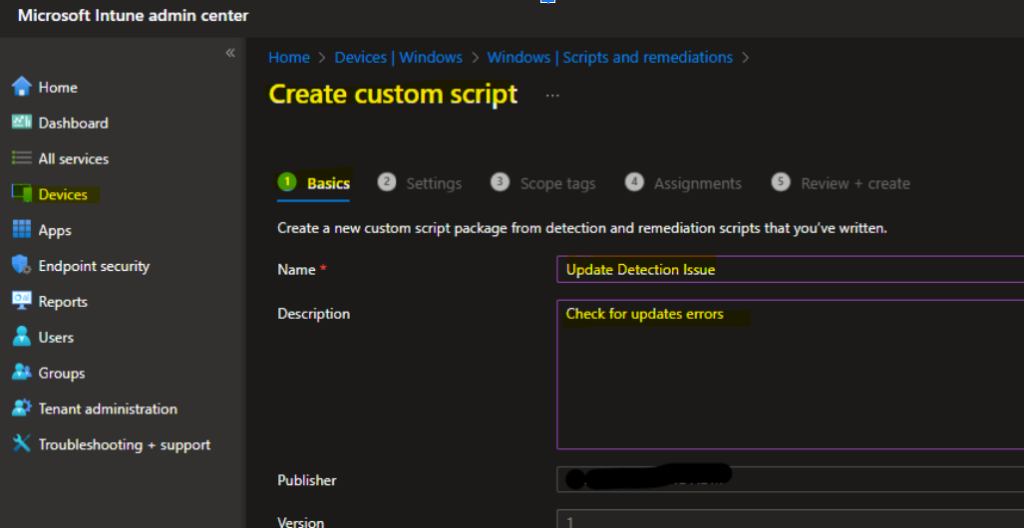
- Create a Remediation Script:
- Go to Intune Admin Center → Windows → Scripts and remediations → Add.
- Upload the detection and the remediation script into the PowerShell Script section.
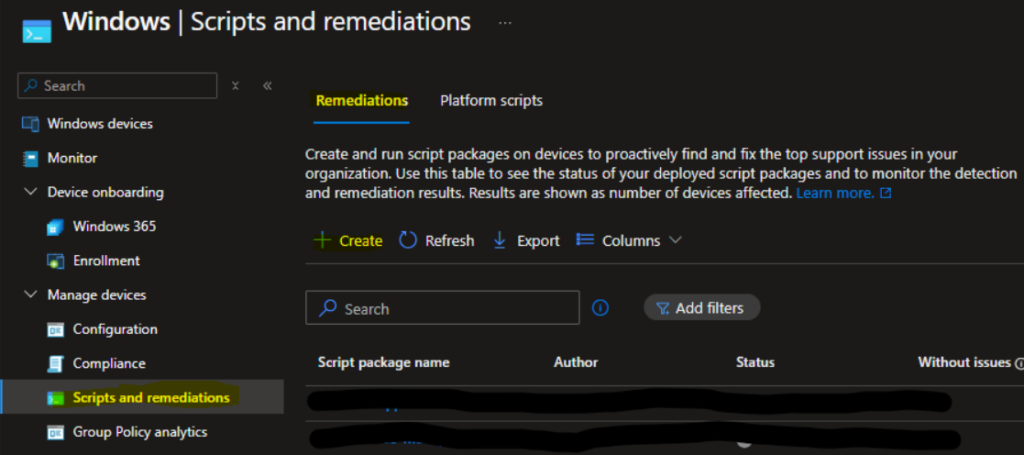
- Deploy the Scripts:
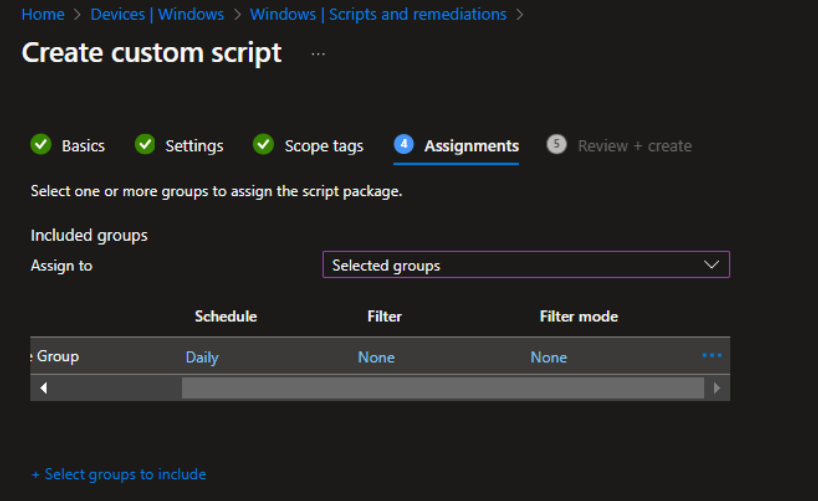
- Deploy both the detection and remediation scripts to your target devices. The detection script will check the system state, and if it fails, the remediation script will execute to fix the issue.
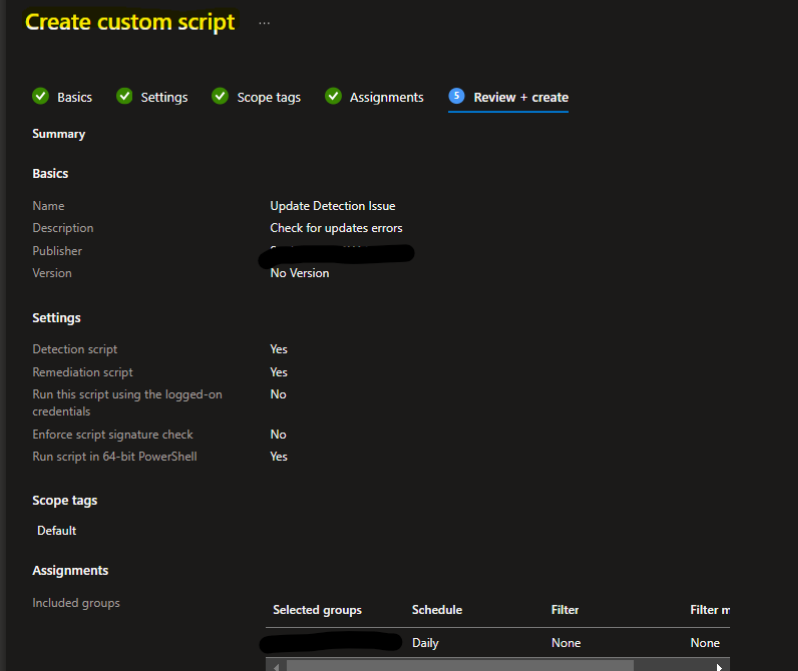
- Monitor the Remediation:
- Use Intune’s monitoring tools to check if the devices are passing the detection rule and if the remediation script is being applied successfully.
With these steps, you should be able to deploy Windows 11 / 23H2 smoothly through Intune, and be ready to troubleshoot any issues with ease. Let Intune handle the heavy lifting, while you enjoy the results!