🔍 Introduction
With the rise of productivity tools and AI integrations in Microsoft 365, organizations are increasingly seeing new apps like Read.ai, Otter.ai, and others automatically embedding themselves into users’ meetings, calendars, and communications.
But how do these apps get access in the first place?
The answer is often buried in a dangerous and often overlooked configuration: user consent to enterprise applications in Microsoft Entra ID (formerly Azure AD). When left unchecked, this setting can expose your entire organization to massive data privacy risks.
🎯 What’s the Problem?
By default, Microsoft Entra (Azure AD) allows users to consent to apps on behalf of the organization — even third-party applications. This means that:
- A single end-user can authorize wide-reaching permissions (e.g., reading calendars, accessing emails, viewing directories).
- Some apps can impersonate bots in every user’s meeting without central approval.
- Consent is granted silently, and security teams may not know until it’s too late.
Case in point? Apps like Read.ai can automatically appear in calendar invites or meetings across the organization, even for users who never installed or authorized them.
🔐 What Are the Risks?
- Data leakage: Third-party apps may read sensitive meeting content or calendar events.
- Shadow IT: Apps appear in meetings or mailboxes without IT’s knowledge.
- Legal and compliance: Sensitive data could be exposed without proper audit trails or DPIA.
- Impersonation risks: AI apps could record or analyze internal meetings under the radar.
✅ How to Check Your Tenant’s Consent Settings
To see if your tenant is exposed:
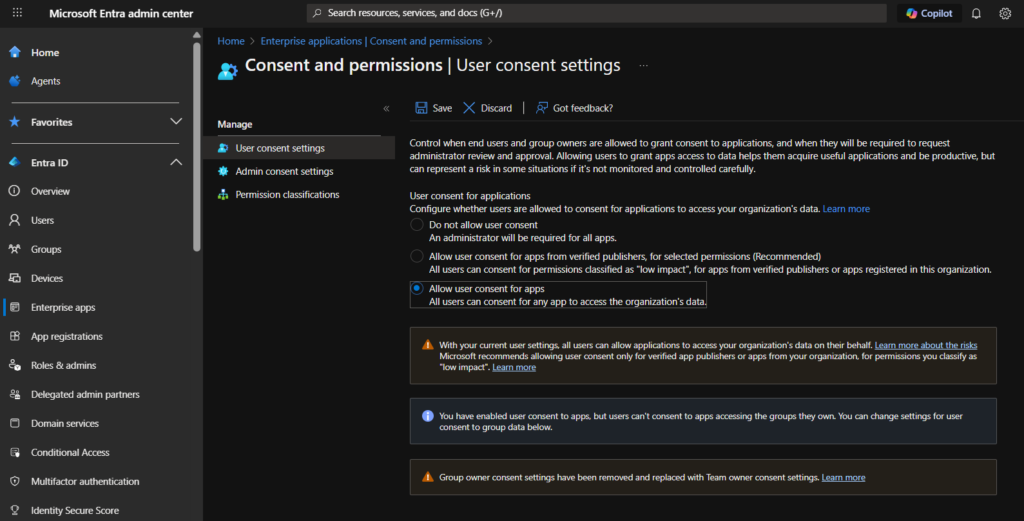
- Go to Entra Admin Center → Enterprise applications | Consent and permissions | User consent settings
- Check if:
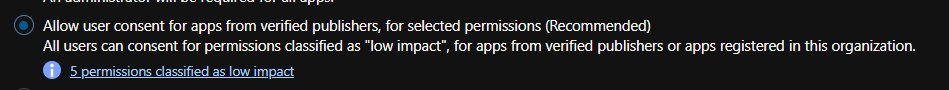
Allow user consent for apps is checked
- If either is set to Yes, you are potentially at risk.
- instead check this:
🛠️ Best Practices and Recommendations
1. Disable User Consent to Org-Wide Apps
- Navigate to:
Entra Admin Center > Identity > Applications > User Settings - Set:
Users can consent to apps accessing company data on their behalf = No
This ensures only authorized personnel can grant access to sensitive org-level data.
2. Enable Admin Consent Workflow
This workflow lets users request app approval, but requires an admin to approve it before consent is granted.
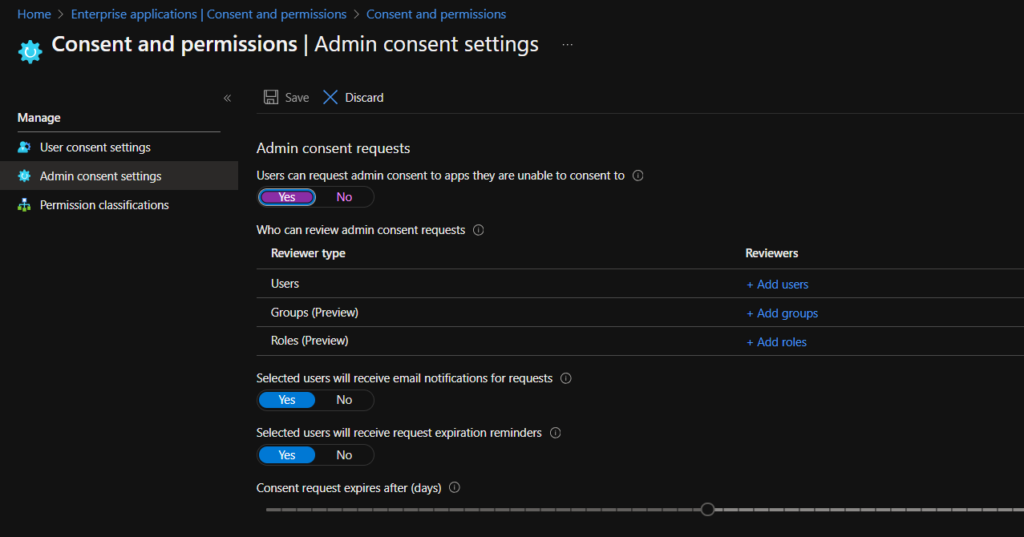
- Enable:
- ✅ Admin consent requests
- ✅ Assign reviewers (e.g., Security or Cloud Admins)
🛡️ This is one of the most effective ways to maintain visibility and control over app permissions.
3. Review Existing Consents (Audit)
Use Microsoft Purview > Audit Search or Entra > Audit Logs to:
- Track who consented to which apps
- Filter by activities like:
Consent to applicationAdd service principalGrant permissions to an application
You can narrow down by app name (e.g., Read.ai) or specific time frames.
4. Use Permission Classifications
Microsoft Entra allows you to classify app permissions:
- Label scopes like
Calendars.ReadWrite,Mail.Read,User.Read.Allas:- High sensitivity
- Medium risk
- Low risk
- Help your reviewers quickly evaluate risk before approving access
🧠 Final Thoughts
It only takes one user clicking « Accept » for a third-party app to gain sweeping access across your organization. In a world of growing AI integrations and data-hungry bots, IT teams must take back control over application consents.
🔒 Disabling org-wide user consent, enabling Admin Consent Workflow, and adopting permission classifications are not just best practices — they are essential security safeguards for any modern Microsoft 365 environment.
💬 Need Help?
If you’re not sure where to start or want help auditing your tenant, feel free to reach out or comment below. Let’s keep our cloud environments secure, together.
🖋️ Souhaiel Morhag
Systems and Networks Administrator | msendpoint.com