As IT administrators, ensuring a seamless and secure user experience is paramount. One common challenge is the frequent security warnings in Microsoft Outlook when users click on hyperlinks, especially those leading to trusted internal resources. Additionally, configuring trusted sites within your organization enhances security and productivity. This guide provides a step-by-step approach to remediate Outlook’s hyperlink warnings and add trusted sites using Microsoft Intune’s Proactive Remediation feature.
Understanding the Hyperlink Warning in Outlook
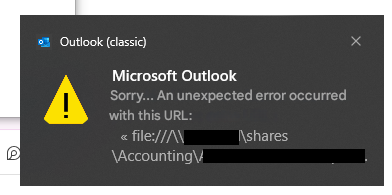
Microsoft Office applications, including Outlook, display a security warning when users click on hyperlinks or objects linking to executable files under a local file server. This behavior is designed to protect users from potential threats but can be intrusive when accessing known and trusted resources. To address this, we can modify specific registry settings to disable these warnings for trusted content.
Utilizing Intune’s Proactive Remediation
Microsoft Intune offers a powerful feature called Proactive Remediation, which allows administrators to detect and remediate issues on devices automatically. By deploying detection and remediation scripts, we can ensure that devices comply with organizational policies without manual intervention.
Step 1: Create Detection and Remediation Scripts
Detection Script:
The detection script checks whether the necessary registry settings to disable hyperlink warnings and configure trusted sites are correctly applied.
# Detection Script: Check for Outlook Hyperlink Warning and Trusted Sites
# Define registry paths
$zoneMapPath = "HKLM:\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMapKey"
$outlookSecurityPath = "HKCU:\Software\Microsoft\Office\16.0\Outlook\Security"
$officeSecurityPath = "HKCU:\Software\Microsoft\Office\16.0\Common\Security"
# Define trusted sites and their expected zones
$trustedSites = @{
"file://fileservername.domain" = 1
"file://internal.local" = 1
"server.internal.local" = 1
"company.sharepoint.com" = 1
}
# Initialize flag
$compliance = $true
# Check if trusted sites are correctly configured
foreach ($site in $trustedSites.Keys) {
$existingValue = Get-ItemProperty -Path $zoneMapPath -Name $site -ErrorAction SilentlyContinue
if (-not $existingValue -or $existingValue.$site -ne $trustedSites[$site]) {
$compliance = $false
}
}
# Check if Outlook hyperlink warning is disabled
$outlookHyperlinkWarning = Get-ItemProperty -Path $outlookSecurityPath -Name "DisableHyperlinkWarning" -ErrorAction SilentlyContinue
if (-not $outlookHyperlinkWarning -or $outlookHyperlinkWarning.DisableHyperlinkWarning -ne 1) {
$compliance = $false
}
# Check if Office hyperlink warning is disabled
$officeHyperlinkWarning = Get-ItemProperty -Path $officeSecurityPath -Name "DisableHyperlinkWarning" -ErrorAction SilentlyContinue
if (-not $officeHyperlinkWarning -or $officeHyperlinkWarning.DisableHyperlinkWarning -ne 1) {
$compliance = $false
}
# Output compliance status
if ($compliance) {
Write-Output "Compliant"
exit 0
} else {
Write-Output "Non-Compliant"
exit 1
}
Remediation Script:
The remediation script applies the necessary registry changes to disable hyperlink warnings and configure the trusted sites.
# Remediation Script: Configure Outlook Hyperlink Warning and Trusted Sites
# Define registry paths
$zoneMapPath = "HKLM:\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMapKey"
$outlookSecurityPath = "HKCU:\Software\Microsoft\Office\16.0\Outlook\Security"
$officeSecurityPath = "HKCU:\Software\Microsoft\Office\16.0\Common\Security"
# Define trusted sites and their zones
$trustedSites = @{
"file://fileservername.fqdn" = 1
"file://internal.local" = 1
"server.internal.local" = 1
"company.sharepoint.com" = 1
}
# Ensure the ZoneMap registry path exists
if (-not (Test-Path $zoneMapPath)) {
New-Item -Path $zoneMapPath -Force | Out-Null
}
# Add or update trusted sites
foreach ($site in $trustedSites.Keys) {
New-ItemProperty -Path $zoneMapPath -Name $site -Value $trustedSites[$site] -PropertyType DWord -Force | Out-Null
}
# Disable hyperlink warning in Outlook
if (-not (Test-Path $outlookSecurityPath)) {
New-Item -Path $outlookSecurityPath -Force | Out-Null
}
New-ItemProperty -Path $outlookSecurityPath -Name "DisableHyperlinkWarning" -Value 1 -PropertyType DWord -Force | Out-Null
# Disable hyperlink warning in Office
if (-not (Test-Path $officeSecurityPath)) {
New-Item -Path $officeSecurityPath -Force | Out-Null
}
New-ItemProperty -Path $officeSecurityPath -Name "DisableHyperlinkWarning" -Value 1 -PropertyType DWord -Force | Out-Null
Write-Output "Remediation applied successfully."
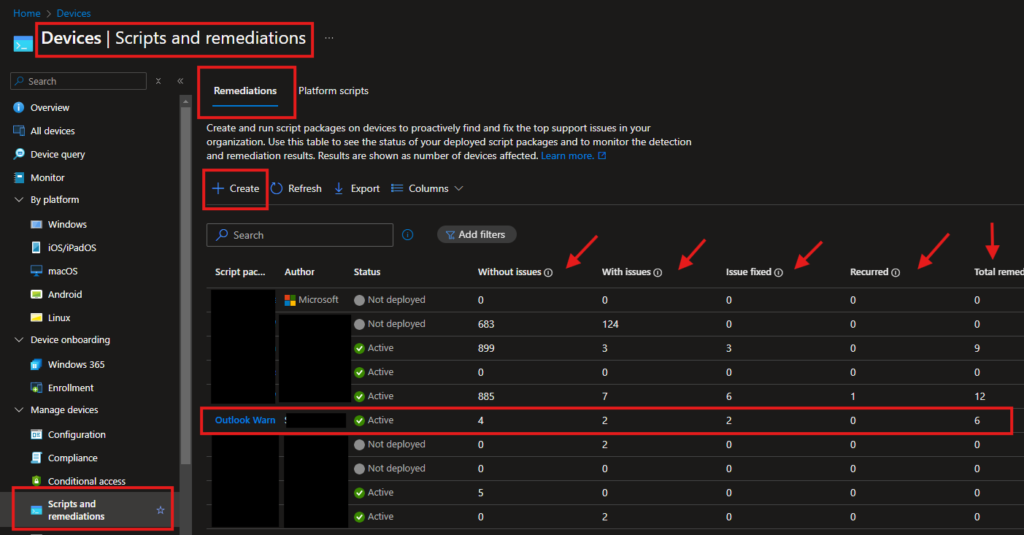
Step 2: Deploy Scripts via Intune
- Access the Intune Admin Center:
- Navigate to the Microsoft Intune admin center.
- Navigate to Scripts and Remediations:
- Go to Devices > Manage devices > Scripts and remediations.
- Create a New Script Package:
- Click on Create script package.
- Provide a Name and Description for the package.
- Upload the Detection and Remediation scripts you created earlier.
- Assign the Script Package:
- Assign the package to the appropriate device groups within your organization.
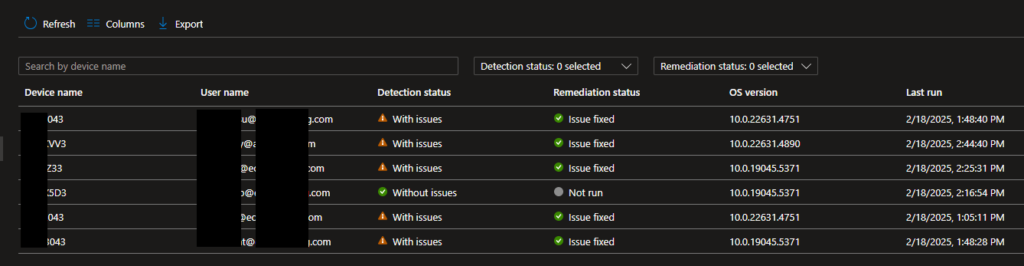
- Monitor Deployment:
- After deployment, monitor the status by navigating to Devices > Manage devices > Scripts and remediations.
- Review the compliance status and ensure the remediation is applied successfully.
By following these steps, IT administrators can automate the process of disabling unnecessary security warnings in Outlook and configuring trusted sites, thereby enhancing both